Thursday, October 29, 2009
Ubuntu 9.10 Released: Why do I care?
Tuesday, October 27, 2009
Security Warning: Facebook Fishing Attempt
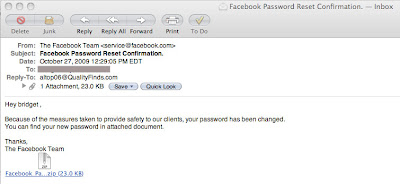
All students of cyber-jutsu should be on guard against a recent fishing attack received by CyberCede Corporation.
The email looks official at first glance; but, we know Facebook would never send out such a message that was not at least first requested by the end user (you). The fishers are hoping that we open the attachment they have sent us, which is pretending to be a new password for us.
A closer examination of this email, in fact shows us that it is bogus. Here we are using Apple's Mail program. Within that application we can view the "long headers" as an option off of the "View" menu, by following the "Message" delta which opens a sub-menu. Users of other email programs should have some similar way to view more details regarding the transmission and receipt of the message.
We've blacked out some of the address particulars so as not to add to the amount of spam we are already processing, and I've circled the "Reply to" and "Return Path" fields in red. (see below)

We can see that the "Reply to" and "Return Path" fields are not consistent with the facade that this email is from Facebook.
We call this a "fishing attack", because the malicious agents are sending this email to potentially hundreds of thousands or more people in hopes that someone will "bite". Just like fishing, many fish may pass by the bait. All it takes is one big one on the hook to make the day pay off.
Exactly what the payload is, has not yet been determined. The payload is the file that they have sent. Since it is in "zip file" format, it could be a buffer overflow attack against a popular "unzip" program. Or the zipped file could be a less creative trojan horse or other malicious executable.
Regardless of what the payload is - we know this is not from Facebook. We all know to just delete the mail without replying to it or opening the attachment.
Stay safe,
Sensei Metajunkie
Thursday, October 22, 2009
Reports of Chinese Cyberspying against U.S. Corporations
Google AdSense Account Disabled
"Because we have a need to protect our proprietary detection system, we're unable to provide our publishers with any information about their account activity, including any web pages, users, or third-party services that may have been involved.
As you may know, Google treats invalid click activity very seriously, analyzing all clicks and impressions to determine whether they fit a pattern of use that may artificially drive up an advertiser's costs or a publisher's earnings. If we determine that an AdSense account may pose a risk to our AdWords advertisers, we may disable that account to protect our advertisers' interests.
Lastly, please note that as outlined in our Terms and Conditions, Google will use its sole discretion when determining instances of invalid click activity."
So, we really have no idea why our account was disabled. If any of our readers have been randomly or blindly clicking on advertisements, you have not helped us. In fact, you may have shut down what might have been a great source of passive income for our blogs.
We have petitioned google to reinstate our account. If that happens, I encourage you all to only click on advertisements which are of interest to you. Don't be afraid to click on advertisements, that is why they are there - but please refrain from just clicking because you know it is generating revenue for us.
I don't usually cross-post between these blogs - but I will put this message on all of the blogs.
Thank you for your understanding and cooperation.
Sensei Metajunkie
Wednesday, October 21, 2009
Metasploit acquired by Rapid7
Friday, October 16, 2009
Utility: Google Translate for International Communications
I am happy to say, we don't need to wait for Google Wave to be released to translate in-between various languages.
You can check out Google Translate at:
http://translate.google.com
Thursday, October 15, 2009
Green Belt Exercise: Install Metasploit

Metasploit is an amazingly powerful and free security tool that must be on the weapons rack of the penetration tester. For the casual cyber-jutsu practitioner, who is not seeking to engage in hard core hacking, contract penetration testing, or cyber-warfare, Metasploit is not a required tool. However, we'll be looking at this tool in detail. Green belts interested in becoming CyberCede Samurai should understand what Metasploit is, and learn to execute reconnaissance and attacks to deliver payloads from within the framework.
Wednesday, October 14, 2009
Black Belt Topic: New Technology - Google Wave
Tuesday, October 13, 2009
White Belt Exercise: Patching for Microsoft's Black Tuesday
A Healthy Body - A Healthy System
Monday, October 12, 2009
Welcome to the cyber-dojo
- Cybersecurity
- Information Security
- Cyber-Warfare
- Bot Nets
- Malware
- Strategies for victory in cyberspace
- Tactics for victory in cyberspace
- Offensive and Defensive Techniques for use in cyberspace
- Compliance with regulations such as HIPAA, HITECH, GLBA, and SOX
- Balance, Awareness, Reaction
- Intrusion Detection Systems
- Network Security Monitoring
- The way of the warrior